ZTE 5G Products Safely Construct the Future Credible Network Cornerstone
Time:2019-04-15
5G defines three application scenarios: eMBB (enhanced Mobile Broadband), mMTC (massive Machine Type of Communication), and uRLLC (ultra Reliable Low Latency Communications). These application scenarios put forward higher requirements for the 5G core network and security protection methods. While supporting emerging services such as AR/VR, eMBB also brings more privacy exposure risks. It is especially urgent to protect privacy. mMTC is the foundation of IoT development and requires more lightweight authentication methods to reduce unnecessary signaling interaction. When uRLLC is applied in low-latency service scenarios such as autopilot and telemedicine, data security transmission must be effectively guaranteed.
ZTE regards constructing a secure and trusted 5G network as its goal and creates "Security in DNA" 5G product security by leveraging advanced methodologies and referring to the best practices in the industry. It regards the maximum security strategy as the cornerstone, security standards and compliance as the framework, the security design and architecture as the support, secure coding and testing as the method, and the security event response as the backup force.
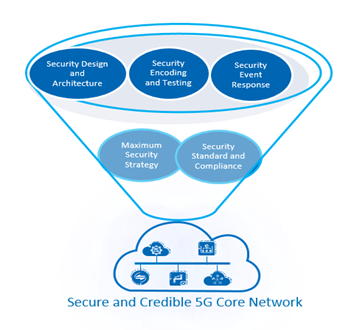
Figure 1 5G Core Network Product Overview
Regarding the maximum security strategy as the cornerstone
ZTE's core network products have always been regarding "focus on customers, comprehensive protection, timely response, security and credibility" as the maximum security strategy
- Focus on customers: ZTE reviews the product safety from the customer's point of view, and practices the fundamental principle of “customer first” that ZTE has been pursuing with more critical standards. It focuses on NFV/SDN and 5G SBA architecture technologies, actively explores the new situation of network security, and proposes innovative solutions such as active advanced threat defense for 5G security protection
- Comprehensive protection: ZTE establishes a unified product security system to serve the entire life cycle of the product. At the beginning of the design of a 5G core network, ZTE regards security as the primary goal, which is based on the security R&D process to create a secure and trusted product. With the acceleration of 5G commercial processes and the rapid development of emerging services, the 5G core network is built in Microservice mode and responds to security requirements quickly through CI/CD to meet the evolving network security situation of 5G.
- On-time response: In the face of security incidents, ZTE makes response for the first time and eliminates security threats in a timely manner. It implements the security incident response as an inherent mechanism. Through this fast response mechanism, the 5G core network can effectively cope with potential security events in the 5G network more accurately and quickly.
- Security and credibility: Providing safe and reliable products and services is the original intention and goal of ZTE's product security. ZTE adheres to high-reliability design goals and strives to provide customers with a trusted 5G network.
Through the continuous implementation of the maximum security strategy, ZTE's 5G core network can help customers build a highly trusted core network environment.
Regarding security standards and compliance as the framework
ZTE's 5G core network adopts multiple industry security standards and legal regulations in an open manner to ensure product safety:
- ZTE regards standards such as ITU-T X.805 and STRIDE as the basis for security architecture and security design while strictly complying with ISO27001, ISO15408 and other information technology security standards.
- ZTE complies with regulatory requirements or compliance requirements such as GDPR and PCI DSS, and comprehends the limitations of these laws and regulations in software development. It maps the applicable parts of the regulatory requirements to software control specifications and ensures that compliance work is completed efficiently through software security guidelines.
For example, in order to effectively identify and protect personal identification information (PII), the core network products are designed according to the "purpose control" and "data minimization" principles of GDPR, and the display range and export capability of personal data are determined according to different user rights. A desensitization tool is provided that processes personal data through a secure algorithm and a salt-encryption mechanism to ensure that the derived data meets the requirements of the GDPR specification.
Regarding the security design and architecture as the support
ZTE is committed to the end-to-end security design and architecture. It independently develops hardware-level protection chips, eliminates illegal versions through the hardware chips, identifies high-definition applications, and prevents malicious code from tampering with system files. Its self-developed OS CGSL also provides a variety of compilation techniques, randomizing global symbol tables, key data structures, and address space to prevent against the insertion and spread of malicious code. ZTE makes independent research and development of an active safeguard platform, to prevent outreach attacks, intranet penetration and unknown threats through semantic modeling, machine learning, probability analysis and other means.
These bottom-up security designs and architectures are the guarantee of the security of 5G core network.
Regarding secure coding and testing as the method
Encoding is an important part of product security. It is often the most vulnerable to buffer vulnerabilities such as buffer overflow, integer overflow, SQL injection, and ROP/JOP (Return Oriented Programming for Return/Jump Oriented Programming).
ZTE has long-term security training for developers and uses industry-leading code scanning tools to identify and reduce such security risks.
During the encoding, the security coding specification corresponding to each language is strictly followed, and the static code security scanning tool is embedded in the Devops tool chain. The code security scanning is used as a necessary condition for submitting the code and entering the product library, to truly realize “integrating safety into the blood” during the encoding period.
In addition to the conventional vulnerability scanning, a large number of abuse use cases and automated safety test cases are designed. Each test will verify the existing security functions once, so that there is no omission or dead ends. Through the "Red Army" troops, in the case that the project has no perception, the targeted damage and privilege escalation tests are implemented to the equipment to simulate the external attack scenario and expose potential safety hazards ahead of time.
Regarding the security event response as the backup force
The product may face some security incidents during the commercial period after being released. These events are not introduced during the development and verification phases, but require timely response.
ZTE's outfield security incident response is handled by ZTE PSIRT (ZTE Product Security Incident Response Team). Its responsibilities include responding to and handling security incidents submitted by customers, responding to and handling security incidents published by industry associations, and developing corporate information security incident management strategies and security incident handling solutions, and analysis of vulnerabilities and patches issued by system software vendors and professional security vendors.
The 5G core network can be launched as soon as possible according to the actual situation of external security incidents and the unified requirements of PSIRT:
- Emergency security solution: Respond quickly, provide temporary mitigation measures, and reduce on-site losses;
- Complete solution: Analyze the root cause, make and release product patches/new versions, and completely solve the hidden dangers in the field.
ZTE's 5G core network follows the maximum security strategy and integrates security elements throughout the life cycle of the product. It truly achieves the aim of “integrating safety into the blood” and becomes the most trusted product for its cu

