5G network is the key to digital transformation and will promote great changes and innovations in all walks of life. In addition to the "Internet of Human", multiple new applications including “Internet of Things" and “Industry Network” have also come into being, such as Internet of Vehicles, telemedicine, smart meter, automatic driving, and video surveillance. In such a diversified business model, 5G network will also face more complex challenges of network security and privacy protection.
To enhance the security of 5G network, 3GPP has defined a new 5G security authentication framework. Its authentication architecture is shown in the following figure:
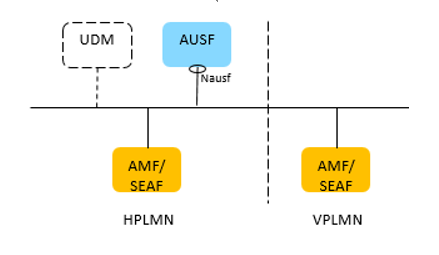
Compared with the authentication/encryption/integrity protection mode of 3G/4G network, the 5G end-to-end network security authentication architecture is more secure and reliable:
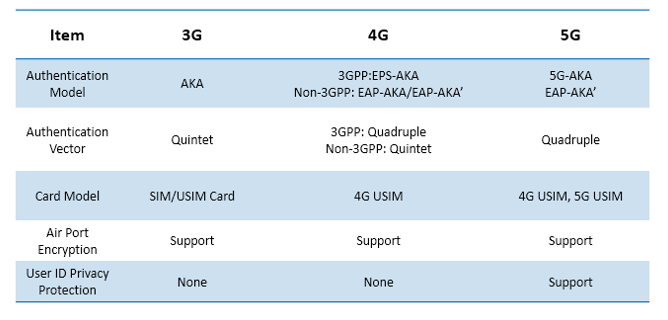
The main content is summarized as follows:
1. Based on the unified authentication architecture, 5G network provides bidirectional authentication between user and network.
2. The solution supports multiple authentication methods, such as 5G-AKA and EAP-AKA’.
3. The hierarchical key derivation mechanism is used.
4. The solution provides encryption of air interfaces.
5. Privacy protection for user IDs is added.
To meet the ultra-high requirements of 5G for network security, ZTE proposes a unified user security authentication solution based on ZTE Cloud Native SDM. This solution not only provides the end-to-end authentication and encryption mechanism for 5G network, but also implements unified authentication under the 2G/3G/4G/5G/IMS multi-network access to ensure the security and reliability of the entire network.
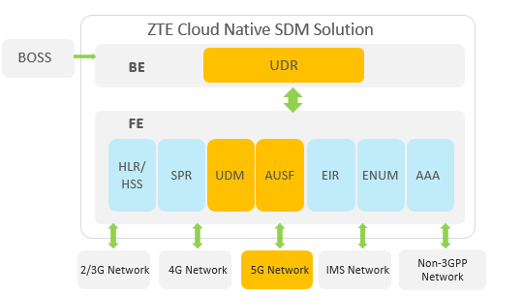
As shown in the figure, ZTE Cloud Native SDM consists of BE (BackEnd) and FE (FrontEnd). BE is based on the unified cloud-based data layer, where the structured storage unit UDR integrates such user data as 2G/3G/4G/5G/IMS. FE is deeply integrated with NE service functions such as HLR, HSS, UDM and AUSF to implement unified mobility management, authentication and authorization management under multi-network access.
- UDR: It integrates and stores multiple structure-based data, including 2G/3G/4G/5G subscriptiondata, PCRF policy data and user authentication data.
- UDM: As the data management NF in the 5GC network, it implements the unified access and authentication function of 5G network, including authentication certificate calculation, 5G HE Avs generation, and re-synchronization authentication certificate calculation.
- AUSF: As the authentication NF in the 5GC network, it provides the authentication service function, supports the 5G AKA flow and EAP AKA’ flow of the 5G authentication architecture, and provides the service network authorization check, authentication algorithm, enhanced home network control and SUCI (subscription concealed identifier) functions.
The unified user security authentication solution of ZTE Cloud Native SDM is developed for 5G. It protects the integrity, reliability, consistency and security of user data, and ensures the secure and stable operation of the multi-access network at all times. It has the following main features:
- Unified cloud native/Microservice architecture to implement fast service deployment
The solution meets related cloud native features, and supports the deployment of VMs and containers. Service-level services can be further expanded and divided into fine-grained Microservices. Each Microservice or service can be independently deployed, upgraded, migrated, and regenerated, helping operators rapidly deploy networks and new services.
- Large capacity, full integration, and high reliability to reduce TCO
Large capacity: A single device supports up to 100+ million static 2/3/4/5G/IMS users.
Full integration: The solution supports the integration of NEs, such as HLR, HSS, UDM, AUSF, EIR, ENUM, SPR, and AAA, effectively reducing CAPEX and OPEX;
High reliability: The multi-level database backup and restoration mechanism and perfect overload protection mechanism guarantee the device stability.
- Unified authentication and authorization of multi-network access to simplify the network
ZTE Cloud Native SDM stores 2G/3G/4G/5G user data in a centralized manner. When a user accesses from different networks, the system can generate 3G Quintet, 4G quadruple, and 5G quadruple in accordance with the authentication algorithms of different networks based on the unified user authentication information to implement unified authentication and authorization when the user accesses from different networks.
- Privacy protection for the permanent ID of a 5G user to protect user privacy.
The ZTE Cloud Native SDM solution provides the user ID privacy protection function for the 5G USIM card. Compared with the plain-text IMSI used in the air interface message of the 4G network, SUCI is used in the air interface message of the 5G network, which is the ciphertext IMSI, to prevent the illegal base station and equipment from obtaining the user's IMSI information and protect the user's privacy information.
- Bi-directional authentication for 5G user registration to prevent illegal users from accessing the network
When a user accesses 5G network, ZTE Cloud Native SDM performs authentication according to the 5G AKA or EAP AKA’ authentication algorithm. After bi-directional authentication is completed on the user side and network side, the network allows the user to access the network and perform user registration and other services.
- Enhanced home network authentication control to prevent against fraud
The 5G authentication and authorization of ZTE Cloud Native SDM is enhanced in terms of home network control. The home network associates the terminal authentication confirmation with the registration process. If the terminal under this network has not passed the authentication, the home network can reject the registration. At the same time, it can instruct the network visitor to request for authentication again before the registration. This further improves the network security and effectively avoids the spoofing upon visiting the network.
Conclusion:
The unified user security authentication solution of ZTE Cloud Native SDM provides unified user authentication and authorization for various terminals, access ways and applications, simplifies the network architecture, and ensures that user information will not be invaded, tampered or leaked by illegal equipment to provide the most fundamental guarantee for 2G/3G/4G/5G/IMS network security.
ZTE supports AI with full-stack IT offering
5GC Green Engine Solution to Enable Green Internet of Everything in the Dual-Carbon Era
5GC Private Network 2.0 Empowerment and Efficiency Improvement Boosts High-Quality Development of the Industry
5G Empowers Intelligent Mining for High-quality Development of Shaanxi Coal Caojiatan Mining
ZTE and China Mobile embrace digitalization for biodiversity conservation in Panda Reserve
Three Aspects Contribute to ZTE’s Remarkable Breakthroughs in Advanced G4X Server
How 5G Private Networks Are Poised to Transform Enterprises Worldwide: All Scenario Private 5G Helps Operators to Realize Private 5G as a Service
ZTE’s commitment to servers generates robust growth of up to 60 times in past 8 years
ZTE eyes top 5 global server market share
Full-Scenario One-Stop 5G Private Network for Vertical Industries

