Main risks faced by user data
User data is the most important asset in communication network. Its security and reliability is the basis for ensuring the normal operation of the network. If user data is unreliable, it may cause some users' services to be abnormal, and the serious result is that the entire network service can break down, causing huge losses to operators and users. In recent years, incidents in the communication system have taken place due to the loss of key user data both at home and abroad, so the security and reliability of user data cannot be neglected.
At present, the security and reliability of user data mainly faces the following risks:
- Data reliability is insufficient: It can cause risks, for example, user data is easily lost, data between nodes is easily inconsistent, and user data is difficult to recover in the event of a failure.
- Data security is not high: It can cause illegal users to access, eavesdrop and tamper with user data, and there is a risk that personal data will be easily leaked.
In order to resolve various risks of user data and ensure the security and reliability of user data, ZTE has launched the Cloud Unified Data Repository (CUDR) solution.
ZTE CUDR is the solution to ensure data security and reliability
CUDR, which is located in the common data layer in communication network, provides common data storage services for various NFs (Network Functions) and applications in communication network. It is a public data layer based on requirements of 5G/cloud/3GPP data services, which realizes the convergence and unified storage of 2G/3G/4G/5G and IMS network user data, and can flexibly meet different deployment requirements of operators.
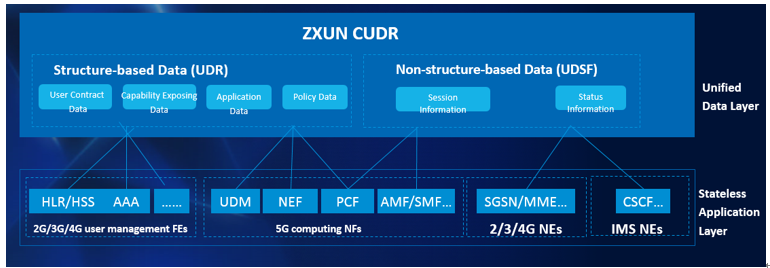
Figure1 ZXUN CUDR Solution Architecture
CUDR includes UDR (Unified Data Repository) and UDSF (Unstructured data storage function). UDR is responsible for storing and processing the structured data, and UDSF is responsible for storing and processing the unstructured data. Based on CUDR, the communication network separates computing from storage, and the application focuses on the processing of business logic. CUDR focuses on the processing and reliability of user data, providing high-performance data access interfaces for applications. The applications and data can be flexibly and independently scaled in/out to achieve full load sharing, greatly enhancing network reliability.
ZTE CUDR supports the storage of massive user data and provides millisecond-level user data access services. It is a fully distributed, big-capacity, high-performance, and highly reliable shared data layer solution.
The storage of massive data raises a higher requirement for data reliability. The reliability of ZTE is mainly displayed as follows:
1. Reliable geographical disaster recovery: ZTE CUDR supports flexible N+K geographic disaster recovery. The data of each site remains strictly consistent. When one site breaks down, services and data can be smoothly taken over by other sites. The disaster recovery switching process does not require manual intervention or does not need to send Reset. The solution is controlled automatically, and the network services are recovered immediately.
2. SON (Self-Organizing Network) with perfect fault monitoring and self-healing capabilities: It can automatically monitor the status of the system, VMs and service components. In the event of an abnormal situation, the system is automatically recovered by automatically isolating the breakdown node, automatically restoring the node, and making self-healing of VMs, without manual intervention and for the convenience of system maintenance.
3. Perfect overload control mechanism: Firstly, the system resources are increased by making automatic scaling-out to automatically improve the system's capability to handle enormous traffic. When the system resources are fully utilized and cannot meet the current high traffic processing requirement, the system automatically starts load control, and enables different levels of service control according to different load levels, ensuring that high-priority services are prioritized and the user's service experience is as good as possible.
4. Multi-level data backup and recovery mechanism: The self-developed high-performance memory database and file storage system are used to process user data. To ensure data reliability, memory database nodes are divided into primary nodes and secondary nodes. The data between the primary nodes and the secondary nodes is fully synchronized. In addition, in order to ensure that user data is not lost when the system is powered off, the storage system persists user data to the local hard disks, cloud storage and external backup servers in real time or quasi real time as required, so that the same data is backed up in multiple-copy mode. When the data node is recovered, multiple data backups are available to ensure that data is not lost.
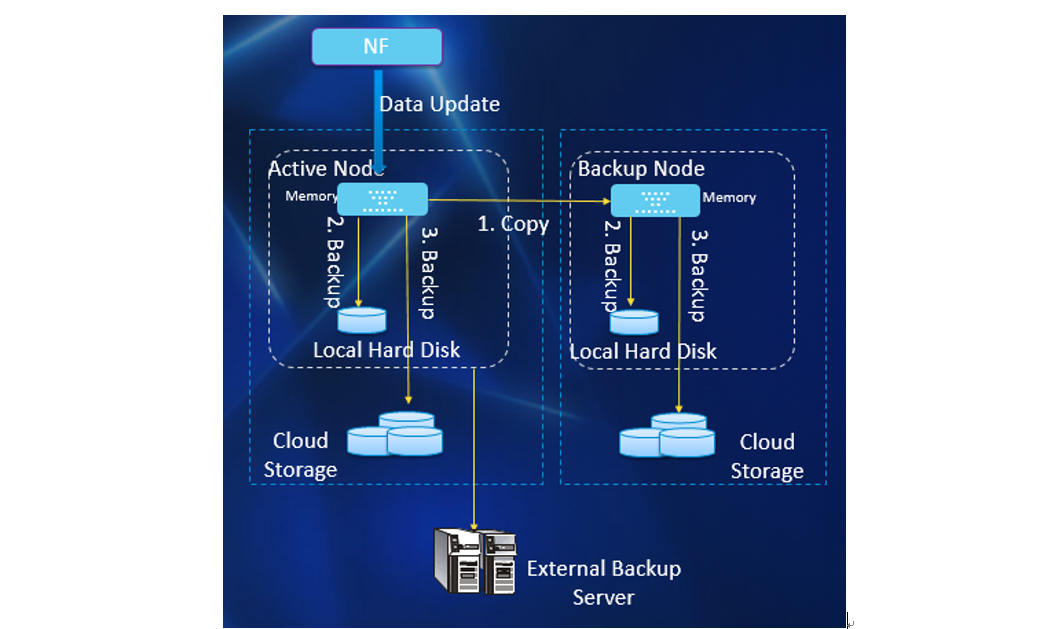
Figure 2 ZXUN CUDR Multi-level Data Backup Solution
5. Multi-layer data verification mechanism
1) When reading and writing data, you can verify data integrity based on the schema in real time.
2) You can make strict verification of data replication and recovery between the primary node and the standby node to ensure data consistency between the primary node and the standby node.
3) The data in the memory database is strictly checked with the data persisted to the disk. If the data is inconsistent, it is automatically restored by rebuilding the standby node.
The data security of ZTE CUDR is mainly displayed as follows:
1. Multi-dimensional data organization security:
1)Tenant isolation: Data organization and access are made by tenants, and data storage and access are strictly isolated. Operation and maintenance are isolated from each other, and data upgrades do not affect each other. Each tenant implements life cycle management separately, and the scaling-in and scaling-out do not affect each other.
2) Access security: The strict ACL (Access Control List) data access control and strict authorization control are made to provide different data views based on permissions. Access control and view control restrict authorized applications from accessing authorized user data only, and limit access operation types such as add, read, update, and delete at the same time.
3)Sensitive data and backup data are encrypted and stored, and the hardware and software security encryption mechanism is provided for sensitive data (such as terminal authentication parameter Ki) to protect user data.
2. Strict personal data protection:
1) Strict access control: Ordinary operators can only view the anonymous operation interface, and only authorized operators can use the plain text operation interface.
2) Only authorized operators are allowed to export user data and can export the plaintext or decrypted user data based on the rights.
3) Only authorized operators can export plaintext or desensitization logs based on permissions.
3. Strict security audit:
1) ZTE CUDR provides system class logs, operation class logs and call class logs to comprehensively record the system running status.
2) It provides storage management of online logs, dump logs, and backup logs.
3) It sets the audit policy according to the log level, keyword, log type, and specific log field.
4) It provides a way to query logs according to various conditions.
Conclusion
The ZTE CUDR solution is born for 5G, providing unified data storage and processing for all NFs in the network. It can ensure the integrity, reliability and consistency of user data, and calmly deal with the impact of natural disasters and heavy traffic to ensure service continuity. In addition, it ensures that user data is safe, users are not easily illegally accessed or tampered with to strictly protect individual data, and user information is not leaked. It is a "safe box" for user data, ensuring that the network services can run safely and stably all the times.
ZTE supports AI with full-stack IT offering
5GC Green Engine Solution to Enable Green Internet of Everything in the Dual-Carbon Era
5GC Private Network 2.0 Empowerment and Efficiency Improvement Boosts High-Quality Development of the Industry
5G Empowers Intelligent Mining for High-quality Development of Shaanxi Coal Caojiatan Mining
ZTE and China Mobile embrace digitalization for biodiversity conservation in Panda Reserve
Three Aspects Contribute to ZTE’s Remarkable Breakthroughs in Advanced G4X Server
How 5G Private Networks Are Poised to Transform Enterprises Worldwide: All Scenario Private 5G Helps Operators to Realize Private 5G as a Service
ZTE’s commitment to servers generates robust growth of up to 60 times in past 8 years
ZTE eyes top 5 global server market share
Full-Scenario One-Stop 5G Private Network for Vertical Industries

