Background and Challenges
In the era of 2G/3G/4G mobile communication networks, relying on the network's strong encryption and authentication measures, 2G/3G/4G networks have always been considered the most secure commercial networks. However, they are mobile-oriented and human-oriented, so the terminal type and the application scenario are relatively simple. As the 5G network enables the Internet of Everything and is oriented to the applications to the full scene and the whole industry, the terminal form and access technologies are diversified, the business and functional requirements of 5G network are increasingly diversified, such as telemedicine, remote engineering remote engineering machinery operation, automated driving, and massive IoT connections. These features will profoundly affect, transform, and be integrated into all aspects of society. Therefore, 5G puts higher demands on network security.
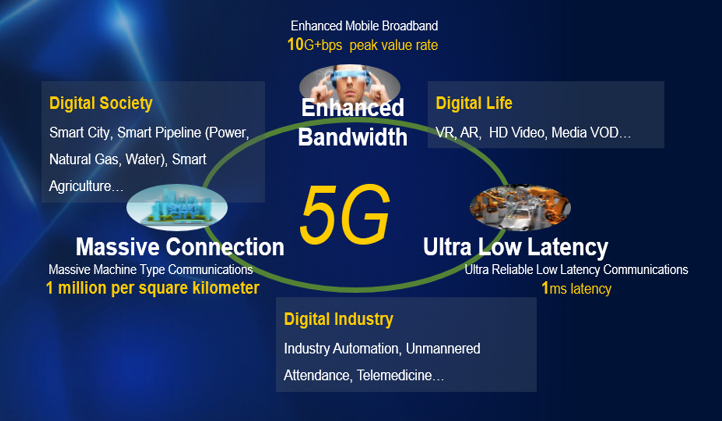
Figure 1 Characteristics of 5G Network
The main challenges faced by 5G network over 2G/3G/4G networks include:
- How to strengthen the verification of the legality of massive terminal access
- How to enhance the protection of user data during transmission
- How to enhance the protection of user privacy information on the wireless air interface
5G E2E Network Authentication & Authorization Architecture Features
In order to enhance the security of 5G network, 3GPP defines a new 5G security-related authentication framework. Compared with the authentication/encryption/integrity protection mode of 2G/3G/4G networks, the 5G end-to-end network authentication & authorization architecture has the following characteristics:
1. Provides mutual authentication between users and networks based on a unified authentication architecture
2. Supports multiple authentication methods, such as 5G-AKA and EAP-AKA’
3. Supports mainstream encryption and integrity protection algorithms such as AES, Snow 3G, and ZUC
4. Provides encryption and integrity protection for air interface and NAS layer signaling
5. Provides user plane encryption and integrity protection between air interface and/or UE and core network
6. Adopts a hierarchical key derivation mechanism
7. Adds user plane data (UP) integrity protection during mobile network transmission
8. Adds User Identity Privacy Protection (SUCI)
The 3GPP organization stipulates that all 2G/3G/4G/5G user data and user authentication data are stored uniformly in the UDR, so that the original 2G/3G/4G users can directly enable 5G services without changing the card or number. However, since the old-fashioned USIM card lacks the home network key required by the user identity privacy protection mechanism, the SUCI protection cannot be supported. Therefore, the user is recommended to replace the original USIM card when the 5G service is activated, but it is not required to change the number to improve safety.
9. Adds the control on the home network
The 5G authentication requires that the AUSF network elements of the home network can be used to verify the RES data returned by the UE, reducing the requirement for the AMF and implementing control on the UE by the home network.
Integrity protection, subscriber identity (SUCI) privacy protection, and home network control of user data planes (UP) are all new features added to 5G network, enhancing the security of 5G network.

Figure 2 5G E2E Network Authentication Frame Defined by 3GPP Standard
ZTE Cloud Native SDM Authentication Solution
Due to the features of 5G network such as ultra-high bandwidth, ultra-low latency and massive connectivity, 5G will be a subversive upgrade with respect to 4G. Network security will be the cornerstone of the digital transformation of the whole society. The authentication solution based on ZTE Cloud Native SDM, which is submitted by ZTE, provides an end-to-end authentication and encryption solution for 5G networks to offer the most fundamental assurance for 5G network security.

Figure 3 ZTE Cloud Native SDM Solution
As shown in the previous figure, the ZTE Cloud Native SDM solution includes two products: ZXUN CUDR (Cloud Unified Data Repository) and ZXUN USPP. ZXUN CUDR is ZTE's unified cloudified data layer solution, which realizes unified storage and management of user data and authentication data of 2G/3G/4G/5G/IMS networks. ZTE Cloud Native SDM integrates functions such as HLR, HSS, UDM, and AUSF to support unified 2G/3G/4G/5G data management equipment and realize unified access and authentication of 2G/3G/4G/5G/IMS networks.
- UDR: It is deployed in the home network, integrating and storing multiple structured data, 2G/3G/4G/5G subscription data, PCRF policy data, and user authentication data.
- UDM: It supports the UDM function of 5G network, realizing unified access and authentication function of 5G network (authenticate the certificate calculation, generate 5G HE Avs, and resynchronize the authentication certificate calculation).
- AUSF: It provides 5G AKA process support for 5G authentication architecture, provides EAP AKA' process support, checks service network authorization, authenticates the algorithm, generates 5G AKA AVs, enhances home network control, and supports SUCI.
Relying solely on the authentication process, fraud cannot be completely prevented. The authentication solution based on ZTE Cloud Native SDM provides the enhanced home network control function by correlating the authentication process with the subsequent registration process. The home network associates the authentication confirmation of the terminal with the subsequent registration process. In the registration process, the solution checks whether the user has recently passed the authentication and authorization under the accessed network. If the user in the network has not passed the authentication and authorization, the registration is refused, and the 5G authentication indication is carried in the rejection message, indicating that the accessed network should obtain a new authentication vector to re-authenticate the user before registration for further improvement of the network safety.
The 5G authentication solution based on ZTE Cloud Native SDM, which is born for 5G, can protect the integrity, reliability, consistency and security of user data, and ensure the network services can run safely and stably at all times, mainly in the following aspects:
- Unified cloud native/Microservice architecture for rapid business deployment and grayscale upgrade
It meets the cloud native related features, supports the deployment based on virtual machines and containers, further expands and subdivides service-level businesses, and splits them into smaller grained Microservices. Each Microservice/service can be deployed and upgraded, migrated and rebirthed independently, helping operators deploy networks and new services quickly.
- High availability, high performance, large capacity design assurance
Reasonable system structure guarantees high reliability and high performance of the equipment. It adopts the distribution mode and the design concept of network function stateless processing. Various services and service components between various services run independently, ensuring excellent overall performance. In the case that one certain processing unit breaks down, the failure does affect other processing units.
The redundant design ensures high reliability of telecom equipment operation. A variety of measures have been taken in the design to ensure the stability of the equipment. For example, the solution provides 1+1 redundancy backup of operation and maintenance components, and N+M redundancy backup of application logic processing, signaling access, and interface forwarding components. The design supports self-healing and geographic disaster tolerance of components. Both the perfect overload protection mechanism and the multi-level database backup and recovery mechanism fully ensure the carrier-level stability of the system.
Large capacity: A single device supports up to 300 million 2G/3G/4G/5G static users at the same time. High performance: Based on the memory database, data access latency is low, while high availability, high performance, and large capacity design guarantee the access and authentication requirements of massive terminals.
- Multi-layer data verification to ensure data consistency
- Unified authentication in multiple access modes
AUSF can handle authentication and authorization requests under 3GPP access and non-3GPP access.
- Privacy protection for user permanent identification
The permanent ID of a user is provided for the service network only after the user authentication succeeds, thereby providing communication security for UEs.
- Enhanced home network control
AUSF supports notifying UDM of the user authentication result, and correlating the user's authentication confirmation with the subsequent registration process to help prevent certain types of fraud.
- Multi-dimensional data organization security protection
Tenant isolation: Data organization and access is made according to tenants, data storage and access is strictly isolated; access security and strict ACL control are implemented; sensitive data and backup data are stored in encryption mode to provide a hardware and software security encryption mechanism for sensitive data to protect user data.
- Strict personal data protection, including strict access control and strict security audit.
Summary:
The authentication solution based on ZTE Cloud Native SDM is born for 5G, providing unified authentication and authorization for multiple terminal types, multiple access modes, and multiple applications. It ensures the integrity, reliability and consistency of user data, calmly copes with all kinds of natural disasters, as well as the impact of large traffic. In addition, it protects the security of user data, and ensures that user information is not easily invaded, tampered, or leaked by illegal users. The solution provides the most fundamental assurance for 5G network security.
ZTE supports AI with full-stack IT offering
5GC Green Engine Solution to Enable Green Internet of Everything in the Dual-Carbon Era
5GC Private Network 2.0 Empowerment and Efficiency Improvement Boosts High-Quality Development of the Industry
5G Empowers Intelligent Mining for High-quality Development of Shaanxi Coal Caojiatan Mining
ZTE and China Mobile embrace digitalization for biodiversity conservation in Panda Reserve
Three Aspects Contribute to ZTE’s Remarkable Breakthroughs in Advanced G4X Server
How 5G Private Networks Are Poised to Transform Enterprises Worldwide: All Scenario Private 5G Helps Operators to Realize Private 5G as a Service
ZTE’s commitment to servers generates robust growth of up to 60 times in past 8 years
ZTE eyes top 5 global server market share
Full-Scenario One-Stop 5G Private Network for Vertical Industries

