NFV/SDN technology enables 5G networks evolving towards the open and universal virtualization mode with physical boundary disappearing.
The network is deployed on cloud infrastructure in the form of virtual function NEs. Network functions (NF) are implemented through software, and can be scaled out/in on demand and flexibly deployed to make efficient use of resources, changing the status of traditional network function NEs being isolated per physical security devices. Virtual networks share physical resources, and physical security boundaries do not exist.
Open NFV architecture increases security risks
NFV makes traditional security protection technologies based on physical entities no longer applicable in new environments. Network virtualization and openness make attacks easier and security threats more easily spread and widely affected.
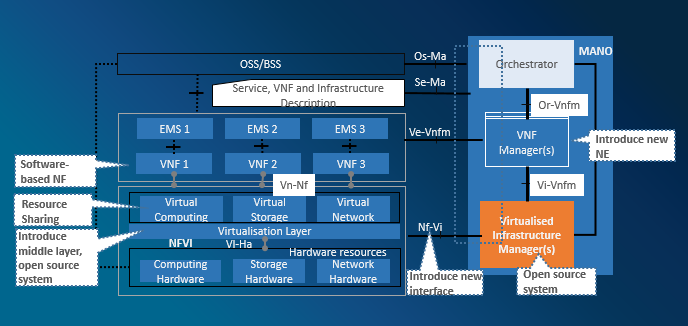
Figure 1 NFV Risks
The multi-layer decoupling of NFV architecture brings openness security risks to component interaction. The introduction of new NEs, software-based NE functions, and virtualization platforms will bring new security risks.
Security risks faced by NFVI mainly lie in hostOS security, trusted running, resource isolation, running data security and networking security.
VNF security risks involve VM lifecycle security, VNF networking security, and service data storage security.
MANO security risks include interface interaction security, permission security, and networking security.
ZTE NFV Security Solution Makes No Security “Blind Zones”
Security is not only related to physical deployment of security features, but more importantly related to security features of virtual asset deployment. It is necessary to establish a security protection system that targets virtual resources and virtual functions, and research into trusted operation and resource isolation of virtual infrastructure.
ZTE NFV security architecture has the following features:
- Pertinence: Targeted at ETSI NFV architecture to enhance security;
- Comprehensiveness: Combination of cloud and network security and hierarchical protection;
- Timeliness: Deployment of emergency plan, quick response to security events;
- Confidentiality: Constructing all-round trusted security communication around the CA center.
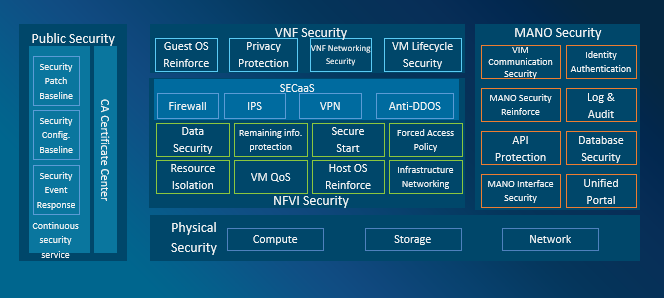
Figure 2 ZTE NFV Security Architecture
Layered optimization to guarantee carrier-grade NFVI security
At the NFVI layer, the HOSTOS system security must be guaranteed first, the Hypervisor resources must be securely isolated, the security data used by NFVI must be ensured, and secure networking is required.
- System reinforcement
Simplified system, configuration optimization, vulnerability scanning, and complicated accounts and passwords
- Log and audit
Monitors core files and directories; audit information can be traced back; logs are uploaded to audit server
- File access
Defines file-level security access policies, and disables file sharing.
- Network whitelist
Customize an easy-to-use policy setting tool and set the range of open ports.
By using security equipment and virtualization isolation technology, the security isolation of Hypervisor resources can be guaranteed to ensure the independent security operation and information security isolation of VMs.
NFVI data security is enhanced in data transmission, storage, backup, and data lifecycle management.
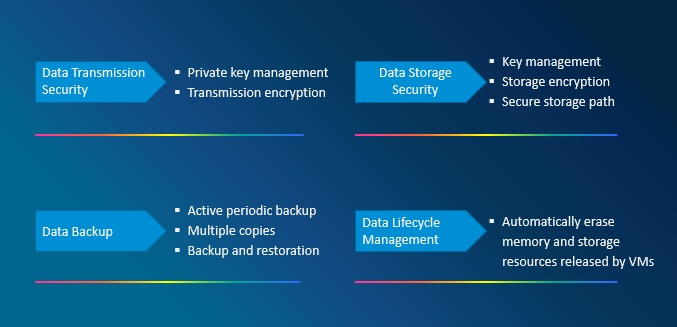
Figure 3 NFVI Data Security
In the NFVI network, physical NICs and Leaf switches are independently deployed, to physically separate cloud management, storage, service and out-of-band management networks. The service Overlay network is divided into more service network planes.
Full life cycle assurance of VNF security
VNF security includes life cycle security, service networking security, personal privacy data security, etc.
- VNF template security
Digital signatures and MD5 provide integrity protection and authentication during registration, loading, and update. The anti-affinity principle is used to restrict VNFs with sensitive data from sharing physical servers with VNFs with external access.
- VM image security
Security vulnerability scanning and security configuration baseline review of VMs; The images and snapshots of VMs are stored in a secure path and in an encrypted manner to prevent malicious tampering. Integrity check must be performed for VM image package during registration, loading, and update.
- VM mobility security
VMs are not allowed to migrate across security domains.Independent VM migration and elastic bearer networks are deployed. Sensitive VM information is encrypted to prevent sensitive data from being leaked during VM migration. Sensitive information is erased from old storage areas to prevent data leakage.
- VM termination security
The physical memory and storage resources originally occupied by the terminated VM may be reallocated to other VMs, and these resources must be completely cleared.
At the security level, the VNF is divided into five security domains: Exposed domain, non-exposed domain, sensitive data domain, service management domain, and platform management domain. It is further divided into an internal VNF interacting network and an external VNF interacting network. The internal VNF interacting network is the traffic interacting between multiple VNFCs in the VNF, including management, control, and media. An external VNF interacting network is an interacting network between a VNF and other VNFs, including signaling, media, management, and charging.
ZTE provides secure storage of VNF data, especially personal data, such as KMS/HSM, to guarantee reliable personal privacy protection.
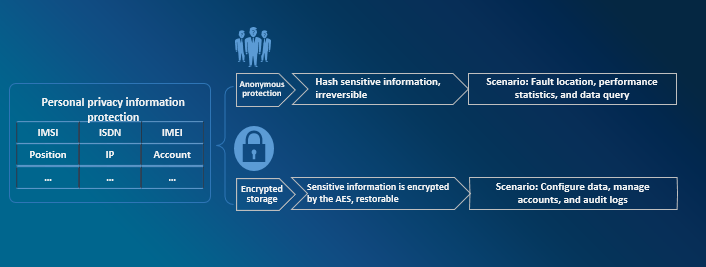
Figure 4 VNF Personal Data Protection
MANO security, guaranteeing operation security
The unified security access portal, component security interaction, and log audit further enhance MANO security.
- Employs such technologies as O&M (operation and maintenance) gateway and single sign-on (SSO) to implement unified security management of the entire network.
- The access authentication and authorization mechanism between components of the cloud management node, together with PKI/CA and TLS technologies, adopts secure data transmission protocols, restricts access modes of APIs, and ensures the integrity and confidentiality of communication.
- NFVO and VNFM are deployed in the way of VM. It minimizes the customization of GuestOS, restricts open ports, access rights and running services, and reduces attack planes of the management node.
- The security log analyze, audits and responds to alarms in real time, helping the administrator to understand security events and running status of the system in real time.
Public security mechanism strengthening daily security
ZTE develops NFV product security R&D processes and creates secure NFV products based on the CSA specifications. The continuously updated security services and the rapid emergency response mechanism further strengthen daily security.
- The scanning tool periodically scans the NFV system integration product, updates the NFV product security vulnerability reinforcement baseline in time, and pushes it to existing offices for upgrade.
- ZTE pays close attention to CVE vulnerability announcement, and will provide, verify and release security vulnerability solutions to customers as soon as possible.
- The NFV product security configuration reinforcement baseline is formed in compliance with the CIS Benchmark, to effectively reduce the probability of security risk occurrence.
- Security event response:Responds to and handles security events submitted by customers; responds to and handles security incidents publicized by industry associations.
There is no doubt that virtualization technologies bring revolutionary elastic architecture and future-oriented capability exposure to 5G networks. ZTE's virtualization security solution provides reliable and secure virtualized networks for the industry in full dimensions, full layers, and all time. ZTE is leading the innovation in mobile communication technologies.
ZTE supports AI with full-stack IT offering
5GC Green Engine Solution to Enable Green Internet of Everything in the Dual-Carbon Era
5GC Private Network 2.0 Empowerment and Efficiency Improvement Boosts High-Quality Development of the Industry
5G Empowers Intelligent Mining for High-quality Development of Shaanxi Coal Caojiatan Mining
ZTE and China Mobile embrace digitalization for biodiversity conservation in Panda Reserve
Three Aspects Contribute to ZTE’s Remarkable Breakthroughs in Advanced G4X Server
How 5G Private Networks Are Poised to Transform Enterprises Worldwide: All Scenario Private 5G Helps Operators to Realize Private 5G as a Service
ZTE’s commitment to servers generates robust growth of up to 60 times in past 8 years
ZTE eyes top 5 global server market share
Full-Scenario One-Stop 5G Private Network for Vertical Industries

