Along with the development of cloud computing, big data, 5G, and other technologies, global telecom network is developing towards personalized user requirements and service types. User requirements and regulatory requirements pose more severe challenges to network security.
To build a secure mobile network, the software version must be secure. The security check before the official software release, especially the penetration test based on the attack and defense mode, is an indispensable protection barrier before the formal deployment of the product.
Common Challenges to penetration test
During the penetration test process, multiple steps such as information collection, vulnerability detection, vulnerability exploitation, and horizontal penetration are performed manually by white hats or professional security test personnel. The test effect depends too much on the security skill level of the individual.
Future attacks are bound to be more flexible and changeable, and new vulnerabilities and new methods will be used to initiate attacks. In this case, it is often difficult to deal with the original penetration test methods and mechanisms effectively. First, the penetration test tools are too dependent on manual operations, resulting in low test efficiency and too much inconvenience of effective maintenance. Secondly, test engineers cannot focus on or control the latest security technologies in the industry.
Intelligent Penetration Boosts Product Security
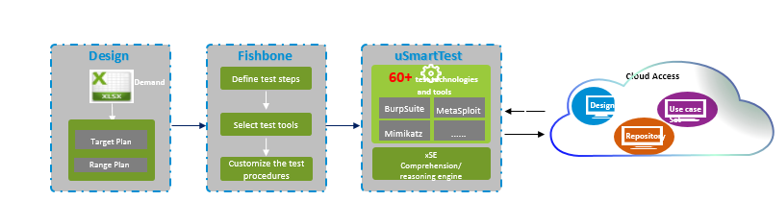
Figure 1 uSmartPen Platform
ZTE's uSmartPen integrates the penetration test tools and solidifies the process, implementing the automation of test planning design, deployment and execution. As shown in Figure 1, its main components are as follows:
- Penetration design tool: It summarizes the configuration parameters and resource requirements required for deployment of the cloud platform, MANO, VNF and test tools according to the scope and objectives of the penetration test, and automatically generates the component instantiation parameter file required for the test scenario.
- Automatic test orchestration tool (Fishbone): It receives the instantiation parameter file generated by the design tool, and prepares for the deployment resources of hardware, cloud platform, MANO, VNF and test tool.
- Intelligent test and learning platform (uSmartTest): After the relevant resources are ready and all components are deployed, the customized test tool is used to test penetration of the target within the specified range, and the xSE intelligent understanding engine and reasoning engine are used to update the model of penetration test to complete the dual objectives of automatic penetration test and model iteration.
- Automatic Test Orchestration Tool --- Fishbone
As shown in Figure 2, Fishbone, in the form of fishbone diagram, splits and combines the penetration steps to implement customization of specific steps and automatic orchestration of the penetration test.
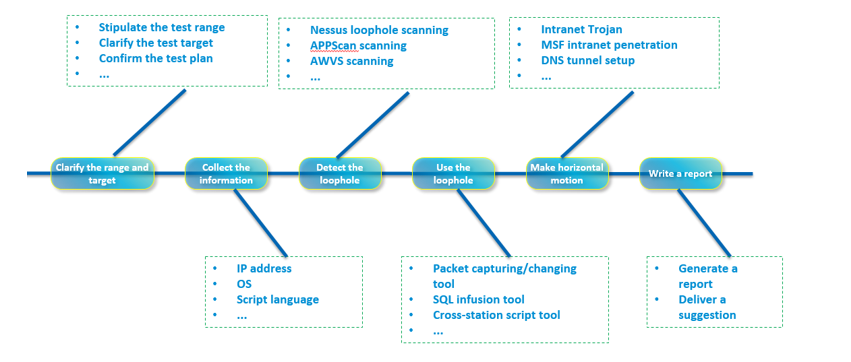
Figure 2 Fishbone Penetration Test Orchestration
First, the sub-steps related to the penetration test are split, and the four steps (information collection, vulnerability detection, vulnerability utilization, and horizontal migration) are displayed as configurable steps.
Second, during the product orchestration penetration test, each substep can be customized in accordance with their special requirements, objectives, and tools. For example, if some users focus on the security of the target system instead of the security status of other systems in the target network, the horizontal movement can be cancelled. Similarly, some cloud service users focus on the APP layer, and can add APIs and cancel the bottom-layer system-level penetration tests without the need to be concerned about hardware or OS security threats.
Finally, the customized sub-steps are mounted to the Fishbone automation framework as nodes, and the framework implements the concatenation and orchestration of the penetration test.
- Intelligent Test Learning Platform (uSmartTest)
- ATT&CK Security Architecture in view of attacker
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a behavior model and knowledge repository that reflects the life cycle of various attacks. After enumerating and classifying these technologies, ATT&CK can be used to "understand" the attacker's behavior later.
According to the security framework, the key control behaviors are selected to match the security requirements. According to the ATT&CK model, the detection capability of the current test model is checked to see whether these behaviors can be effectively covered. You can improve the detection capability in accordance with the troubleshooting result. Finally, the attack technology and tactics to be covered are added and improved, and a penetration test model is established.
To keep abreast of the industry's cutting-edge practices by using the latest technologies, ZTE starts from the risk-based threat model and analyzes possible invasion and adverse impacts. Then, the MITRE ATT&CK framework is introduced to improve various penetration test tactics and tools from the perspective of the attacker and establish a penetration model that conforms to itself.
- Intelligent Engine Realizes Optimization of the Test Model
Starting from the threat model, ZTE analyzes the invasion and impact, uses the intelligent engine xSE to analyze the attack behaviors, deduce the attack chain, and iteratively optimize the penetration test model.
First, ATT&CK is used at the behavior layer for modeling, and TTP of threat information is fully used for knowledge sharing. It is used to portray the attacker to a larger extent. In the next step, the xSE intelligent engine is used to analyze the reasoning, and the security test personnel are released from the specific technical means and indicator rules.
The ZTE intelligent engine xSE integrates the understanding engine with the reasoning engine: The understanding engine is used to convert massive alarms into corresponding attack behaviors, and then the reasoning engine is used to analyze the damage caused by these attacks, and the attack chain is combined to carry out attack judgment and rapidly update the model.

Figure 3 Intelligent Engine xSE
Summary
The commercial use of 5G is accelerating, and the security requirements for products are increasing. Based on user requirements and industry frontiers, ZTE implements full-process automation of penetration test design, planning, deployment, implementation, and iterative update, providing comprehensive and efficient support for network security operation.
ZTE Common Edge enables 5G network
What Voice Solutions and Applications are Needed in the 5G Era?
ZTE Full-Scene UPF, Simplified and On-Demand
Build new IP interworking gateway offices to promote the deployment of IMS in all networks
5G Standards are Becoming Mature with Smooth Development of R16 and R17
Flexible and Highly-efficient MEC Distribution Solution Enables Industry Customers to Customize a Private Virtualized Mobile Network
ZTE Promotes the Performance and Efficiency of Servers and Storage to Help Enterprises Dig Deeper into Data Value
5G Operations Get Smarter When AI and Slicing Combine
Virtualized User Plane I/O Performance Acceleration Technology Boosts 5G Network
Whether Deployment is Centralized when VoLTE is Virtualized?

